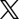Data Risk Assessment report
Depending on the permissions associated with your user role, the Data Risk Assessment report may not be available.
The Data Risk Assessment report shows the list of Windows and Mac devices with an active Endpoint Data Discovery (EDD) policy. If the policy detected confidential or at-risk file content on a device, the report also shows the calculated level of risk, or Risk Score, associated with that file content. The Risk Score is based on the Match Score, but a weight is added if the detected file content was found in a cloud storage A computing model in which data is stored on remote servers that are managed by a cloud storage service provider. Users of the service access their data using the Internet or "cloud". folder and therefore may be at risk of being shared in the cloud.
The scope of this report is limited to information collected during the last full EDD scan The Secure Endpoint Agent process that opens and analyzes files on a device's hard drive to identify at-risk content, as defined in an Endpoint Data Discovery policy. See also DAR component. of each Windows and Mac device, and all subsequent delta scans. If a scan is in progress on one or more devices when you run the report, any data collected up to that point is available in the report. For new activations, it may take up to two days before data is available in this report.
On the Reports page, you can access this report from Absolute view or the Data Visibility category.
Risk Scores are not calculated for the Local AI Models EDD rule.
The Data Risk Assessment report applies only to supported Windows and Mac devices with an active Endpoint Data Discovery policy and an Agent status The operating condition of a device's Secure Endpoint Agent. Possible values are Active (indicates that the device's agent has connected to the Absolute Monitoring Center), Inactive (indicates one of the following: the device was moved to another account; the device was unenrolled, but it is now set to be reactivated; or the device had Persistence enabled at the factory, but it has not yet called in to the Absolute Monitoring Center), and Disabled (indicates that the agent is either flagged for removal or removed from the unenrolled device). Inactive and Disabled devices do not consume a license. set to Active.
To view information in the Data Risk Assessment report you first need to activate the Endpoint Data Discovery policy in one or more policy groups.
There are no filters applied to the Data Risk Assessment report. However, you can create a customized version of the report by adding filters based on one or more filter criteria.
The information collected from each device is organized in the following columns:
| Column | Description |
|---|---|
| Device name |
Includes the device's device name The name assigned to the device in the operating system. For Chromebooks, device name is not applicable and therefore shows as "Chrome" in the Secure Endpoint Console. and serial number The identification number assigned to the device by the device manufacturer. For Windows devices, this value may correspond to the serial number of the BIOS, the motherboard, or the chassis, depending on the manufacturer. To view the device's Device Details page, click the linked device name. |
| Risk Score | The total of all individual EDD rule Risk Score A computed value in which a weight may be added to a Match Score depending on where the confidential or at-risk file content resides on the device. When a file resides in a cloud software storage folder, and therefore may be at risk of being shared in the cloud, its Match Score is multiplied by two (2) to arrive at its Risk Score. If the file resides elsewhere, the file's Risk Score is the same as its Match Score.s for the device. |
| Encryption > Status |
The summarized encryption status of the device |
| Username | The username of the user who was logged in to the device when an agent connection occurred. If no user was logged in during the most recent agent connection, the last detected username shows. |
| Cloud Storage |
Indication of whether file content was detected in a cloud storage software folder When the column contains Yes, the EDD policy detected confidential or at-risk file content residing in a folder that is typically created when cloud storage software is installed on a device. Since this puts the file content at greater risk, presence of the icon increases the applicable file's Risk Score. |
| Estimated Cost Exposure (USD) |
The potential estimated cost to your organization, in US dollars, of a data breach of the at-risk files detected on the device Estimated Cost Exposure (USD) is based on a methodology presented in the Verizon 2015 Data Breach Investigations Report and is intended to serve as a guideline only. The actual cost of a data breach within your organization will vary. For more information about the methodology, open the 2015 Data Breach Investigations Report on the Verizon website and see the section, "Impact: 'In the Beginning, There Was Record Count'” (pages 27 to 30). |
| Scan Date | Date and time (local device time A date and time expressed in a device's local time zone, as opposed to server time. In the console, local device time applies to usage data collected from devices, and the scheduling of some device action requests.) when the device was scanned using the scan configurations set in the Endpoint Data Discovery policy |
| Credit Card Risk Score |
The calculated Risk Score for the applicable EDD rule Risk Score is a computed value in which a weight may be added to a Match Score depending on where the confidential or at-risk file content resides on the device. When a file resides in a cloud software storage folder and therefore may be at risk of being shared in the cloud, its Match Score is multiplied by two (2) to arrive at its Risk Score. If the file resides elsewhere, the file's Risk Score is the same as its Match Score. For example, a device has a Personal Financial Information Match Score of 34. Four of the matches were detected in a file residing in a cloud storage software folder, while the remaining 30 matches were not. The calculated Risk Score for this EDD rule is 38 (30 + (4x2)). |
| Personal Health Information Risk Score | |
| Personal Financial Information Risk Score | |
| Social Security Number Risk Score | |
| Encrypted or Password Protected Risk Score | |
| GDPR Risk Score | |
| Custom Rule Risk Score | The total Risk Score A computed value in which a weight may be added to a Match Score depending on where the confidential or at-risk file content resides on the device. When a file resides in a cloud software storage folder, and therefore may be at risk of being shared in the cloud, its Match Score is multiplied by two (2) to arrive at its Risk Score. If the file resides elsewhere, the file's Risk Score is the same as its Match Score. across all custom EDD rules |
You can search for specific information in the Data Risk Assessment report.
You can also include other information in the report by adding more columns. For example, if you configured any custom rules to be included in the report, you can add their respective Match Score column.
If No Data shows in a column, the information was not detected on the device.
By default, the report data is sorted by the Risk Score column, in descending order. You can change the sort order by clicking a column heading.
You can perform the following tasks on the Data Risk Assessment report:
- Open and view the report
- Adjust the columns on the report
- Add or remove filters
- Export the report
- Email the report on a set schedule
- Favorite the report
- Save changes to report filters and columns to create a custom view or a new report