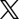Application Compliance report
The Application Compliance report (accessible on the Reports page from the Absolute view or the Application category) shows information about the compliance status of application installations on:
-
Windows and Mac devices with an activated Required Applications policy
-
Windows devices with an activated Application Resilience policy
 Applications > Compliance on the navigation bar.
Applications > Compliance on the navigation bar.The Application Compliance report shows information about the applications installed on your active Windows and Mac devices.
To show data in the Application Compliance report, at least one of the following requirements must be met:
-
One or more Application Resilience policies are activated
-
One or more Required Applications policies are activated
To view the Application Compliance report, your user role needs to be granted the View permission for Software reports. All default user roles are granted this permission.
No filters are applied to the report, but you can refine what's shown by adding filters.
Each row of the Application Compliance report shows the compliance status of a specific application installation on a device, based on an application policy. If a device has multiple versions of the same application installed or multiple policies applied to it (for example, both a Required Applications policy and an Application Resilience policy), each version or policy is reported in a separate row.
The report includes a default collection of information organized in the following columns:
- Device name: contains the device name The name assigned to the device in the operating system.
For Chromebooks, device name is not applicable and therefore shows as "Chrome" in the Secure Endpoint Console. and serial number The identification number assigned to the device by the device manufacturer.
For Windows devices, this value may correspond to the serial number of the BIOS, the motherboard, or the chassis, depending on the manufacturer. for the device
To view more information about a particular device, click the linked device name to open the device's Device Details page.
- Policy name: shows the name of the Required Applications policy or the Application Resilience policy used to determine the compliance status of the application
To view details about a policy, click its name. The policy opens in the Application Policies area.
- Application: shows the normalized name of the application associated with the policy and the version installed on the device
- Policy type: indicates whether the policy used to determine the compliance status of the application is a Required Applications policy (Required) or an Application Resilience policy (Resilient)
- Status: shows the compliance status of the application's installation on the device based on the requirements set in the application policy
 Statuses
Statuses- Compliant: all requirements set in the policy have been met
- Non-compliant: one or more requirements set in the policy have not been met
- Missing: the application is not installed on the device
- Pending: the policy has been activated, but the device has not yet uploaded new application data
Unknown: a compliance status could not be calculated
 About the Unknown status
About the Unknown statusApplication compliance information is unavailable and a status of Unknown is reported when there is an issue with the application's installation, such as:
The Secure Endpoint Agent can't find or access the installation location.
The installation was not completed successfully.
To see all devices with a particular status, add the Status is <status> filter.
- Status details: when a device's Status column shows Non-compliant or Missing, this column shows the reason why the application does not comply with the policy
For all other statuses, the Details column shows No data.
To see all devices that are not compliant for the same reason, add the Status details is <reason> filter.
- Policy group: the policy group that the device belongs to
- Status updated: the date and time when the compliance status of the application’s installation on the device was last updated
You can add more device information to the report, such as OS name The name and version of the operating system detected on a device. The operating system is software that manages the software and hardware installed on a computer and allows programs and services to run. It is responsible for the basic operations of a computer system., by adding more columns.
To view all applications installed on a particular device, do one of the following:
- Search the report for the device
- Filter the report by device name
- Click the link in the Device name column to open the device's Device Details page, then click the Applications tab
To view the list of devices on which a particular application is installed, do one of the following:
If the Secure Endpoint Agent detects application changes on a device, the new data is uploaded on the next agent connection, which is typically within the next 15 minutes. The device's application compliance status is reevaluated at that time.
You can search for a device, application policy, application, or policy group.
To search, enter all or part of a keyword in the search field and click Search or press Enter.
By default, the page's data is sorted by policy name, in descending order. To sort the data by another column, click the column heading. To reverse the sort order, click the column heading again.
Depending on the Absolute licenses associated with your account, and your user role, you may be able to perform some or all of the following tasks from the Application Compliance report:
- Open and view the report
- Adjust the columns on the report
- Add or remove filters
- Export the report
- Email the report on a set schedule
- Favorite the report
- Save changes to report filters and columns to create a custom view or a new report
Depending on the Absolute licenses associated with your account, and your user role, you may be able to perform some or all of the following tasks on the devices in this report:
- Search for and view individual devices in the report
-
Request any of the following actions on one or more devices:
- Freeze
- Run script
- Wipe
- Send message
- Unenroll
- Remove freeze
- Delete file
- Perform EDD scan
- Change license
- Change policy group
- Report missing or stolen
- Report found
- Manage supervisor password
- Run playbook
The Change policy group action is not available from this report.